A man-in-the-browser attack occurs when the victim has entered the URL into the browser independently, without an external prompt. On the surface, transactions are taking place normally with expected prompts and password requirements. When an MitB attack is successful, the perpetrator can steal a user's data and money.. An active man in the middle attack consists of a SSL session from client to MITM and from MITM to server. These are fully separate sessions which have different keys and can also use a different cipher, protocol version etc. If the MITM attacker has the servers original private key he can impersonate the server perfectly by using the original.

Кибербезопасность MiTM Man in the middle Атака посредника, или атака «человек посередине

Cosa significa Man In The Middle (MiTM) Wikibit

Attaque Man in the Middle (MITM)

ManintheMiddle Attack Detection and Prevention Best Practices
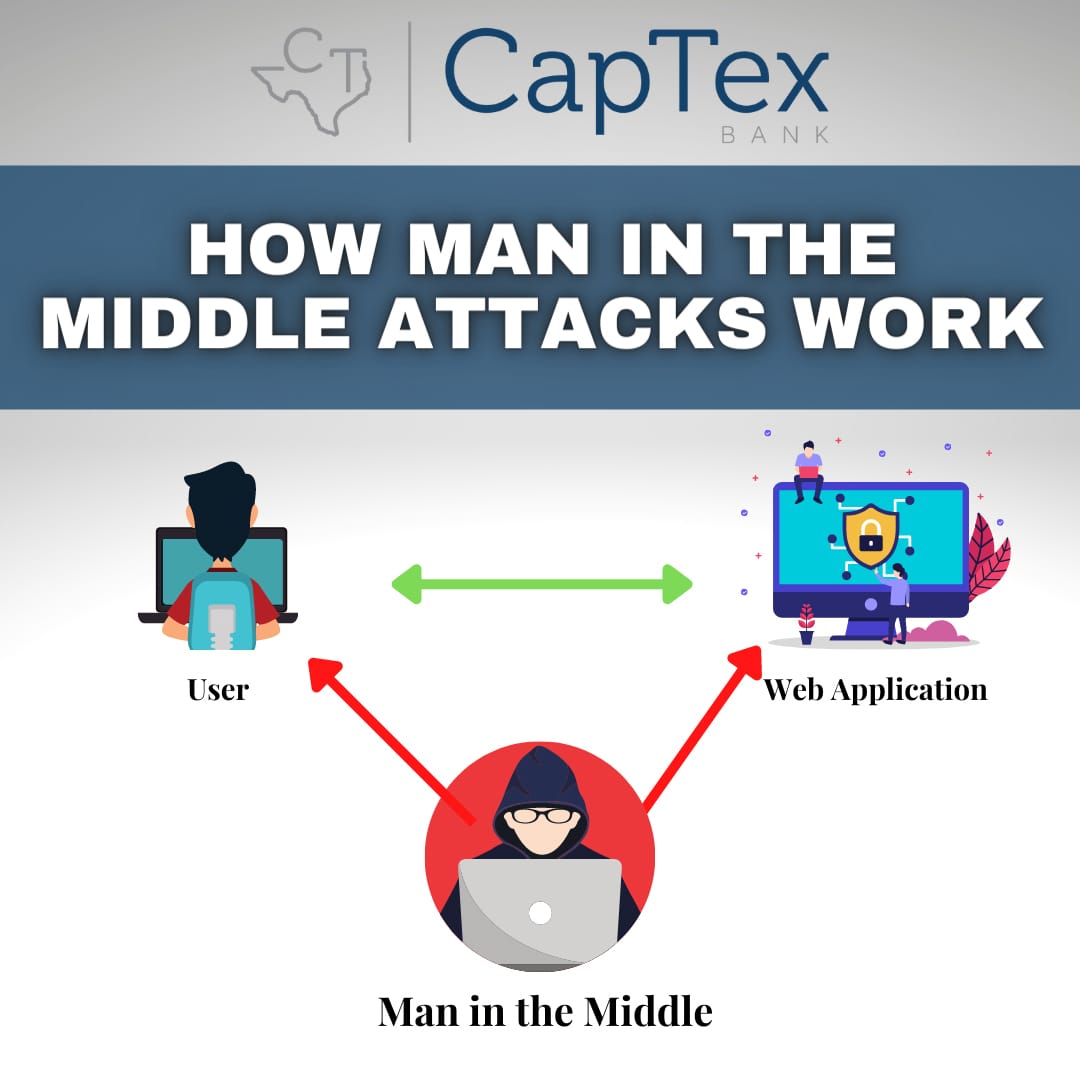
Man in the Middle » CapTex Bank

The Man in the Middle Crossroad Christian Church
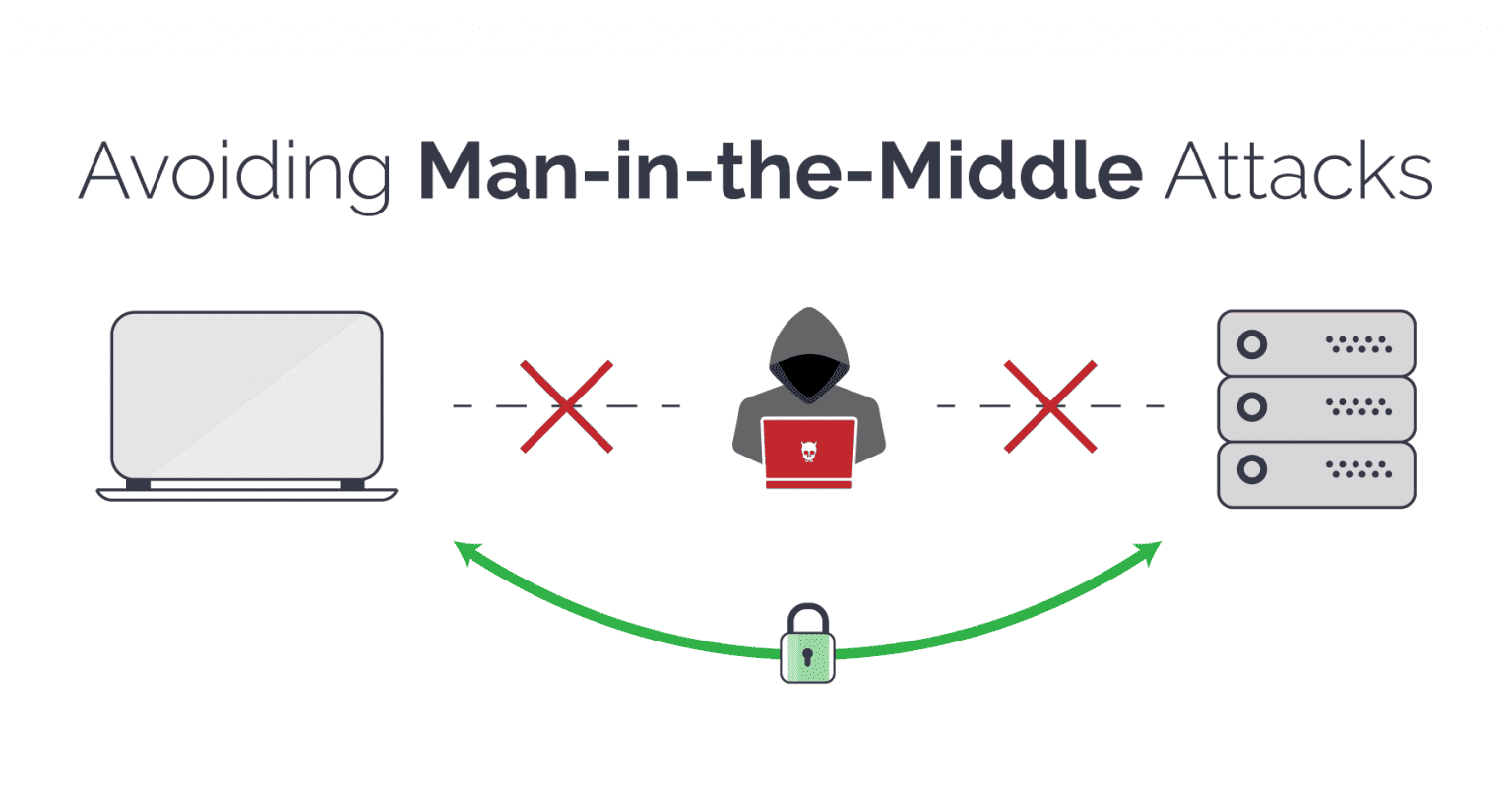
Maninthemiddle Attack How to Protect yourself Gadgetswright
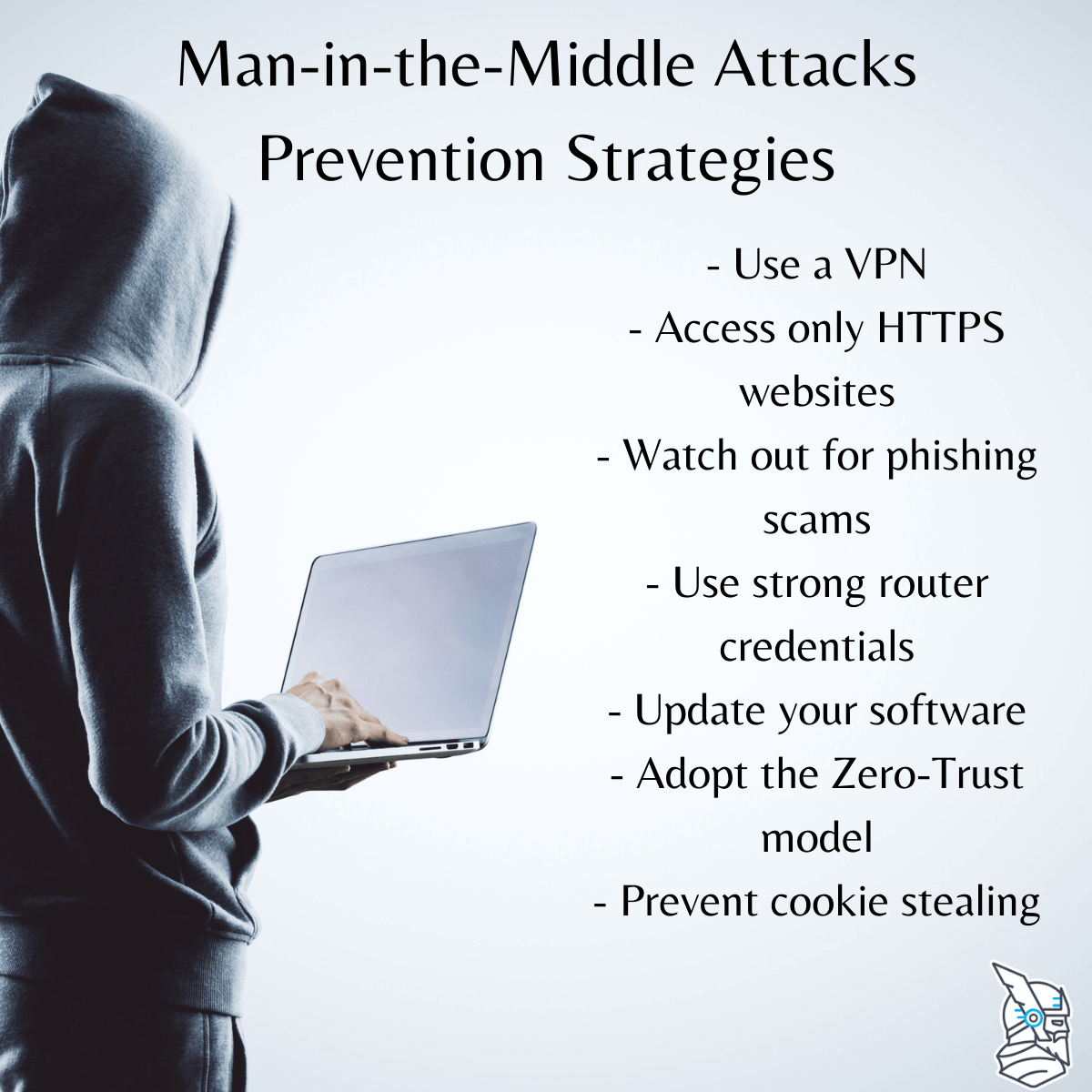
ManintheMiddle Attack Definition, Examples, Prevention
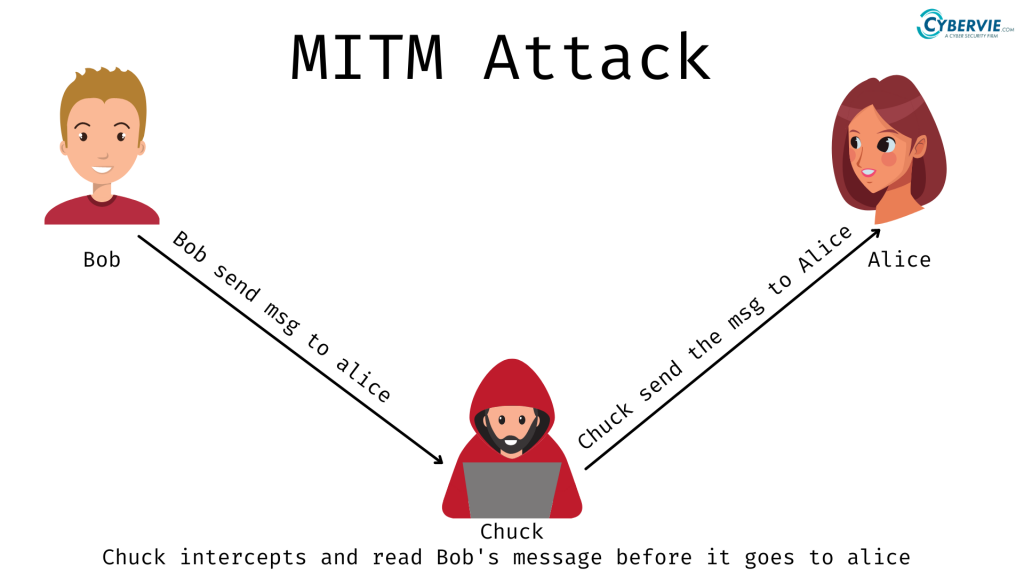
ManInTheMiddle attack Different Types and Techniques CYBERVIE

ManintheMiddle Attacks explained, defined

Infosecblogger Man in the middle

The role of Middlemen! Global Business Review Magazine

Tutorial Man in the Middle YouTube
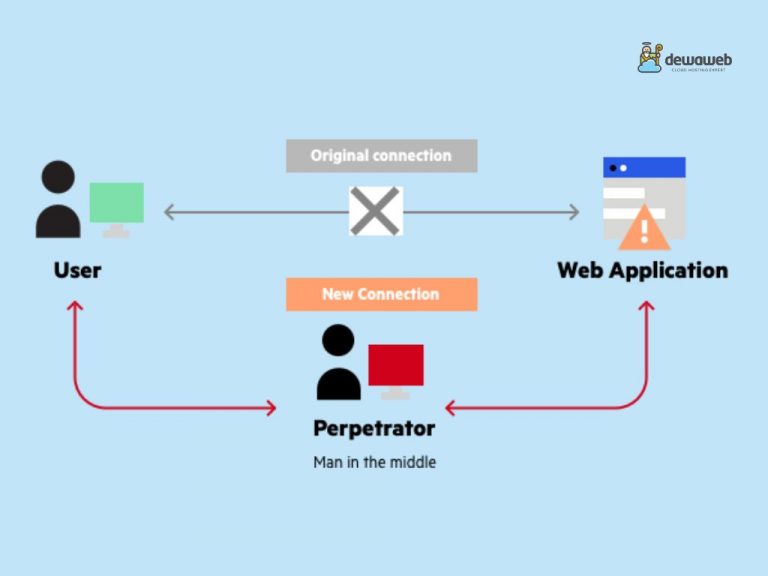
Man in the Middle Attack Pengertian, Jenis dan Cara Menghindarinya

Man in the Middle (1964) — The Movie Database (TMDB)

What is Man in the Middle Attack? Types of Man in the Middle Attack

What is a Man in the Middle (MITM) Attack? SentinelOne
![Video 2 Role Of Middle Man [YOU!] YouTube Video 2 Role Of Middle Man [YOU!] YouTube](https://i.ytimg.com/vi/c6eNQcmxuCU/maxresdefault.jpg)
Video 2 Role Of Middle Man [YOU!] YouTube
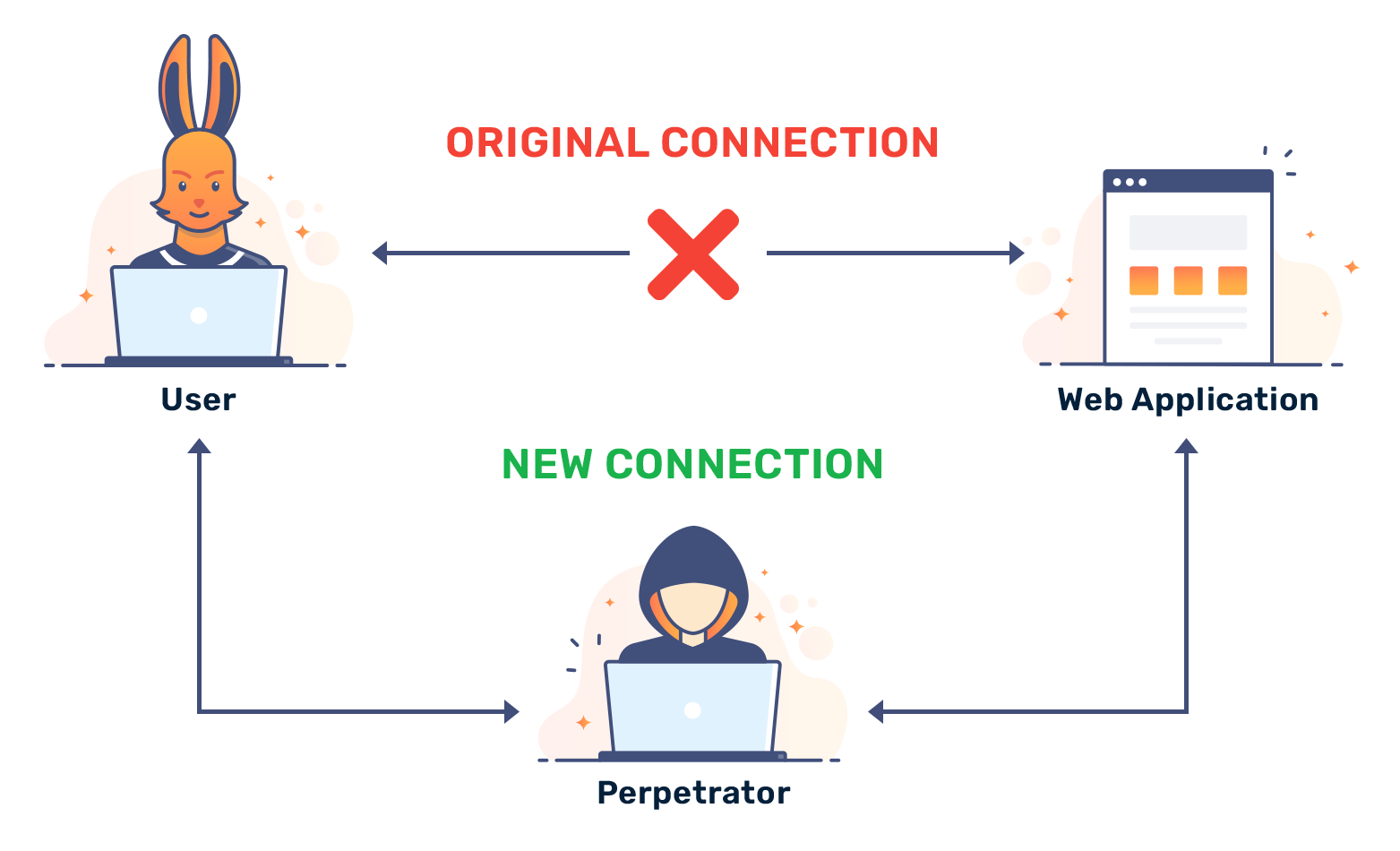
What are Man In The Middle (MITM) Attack and how do they work?
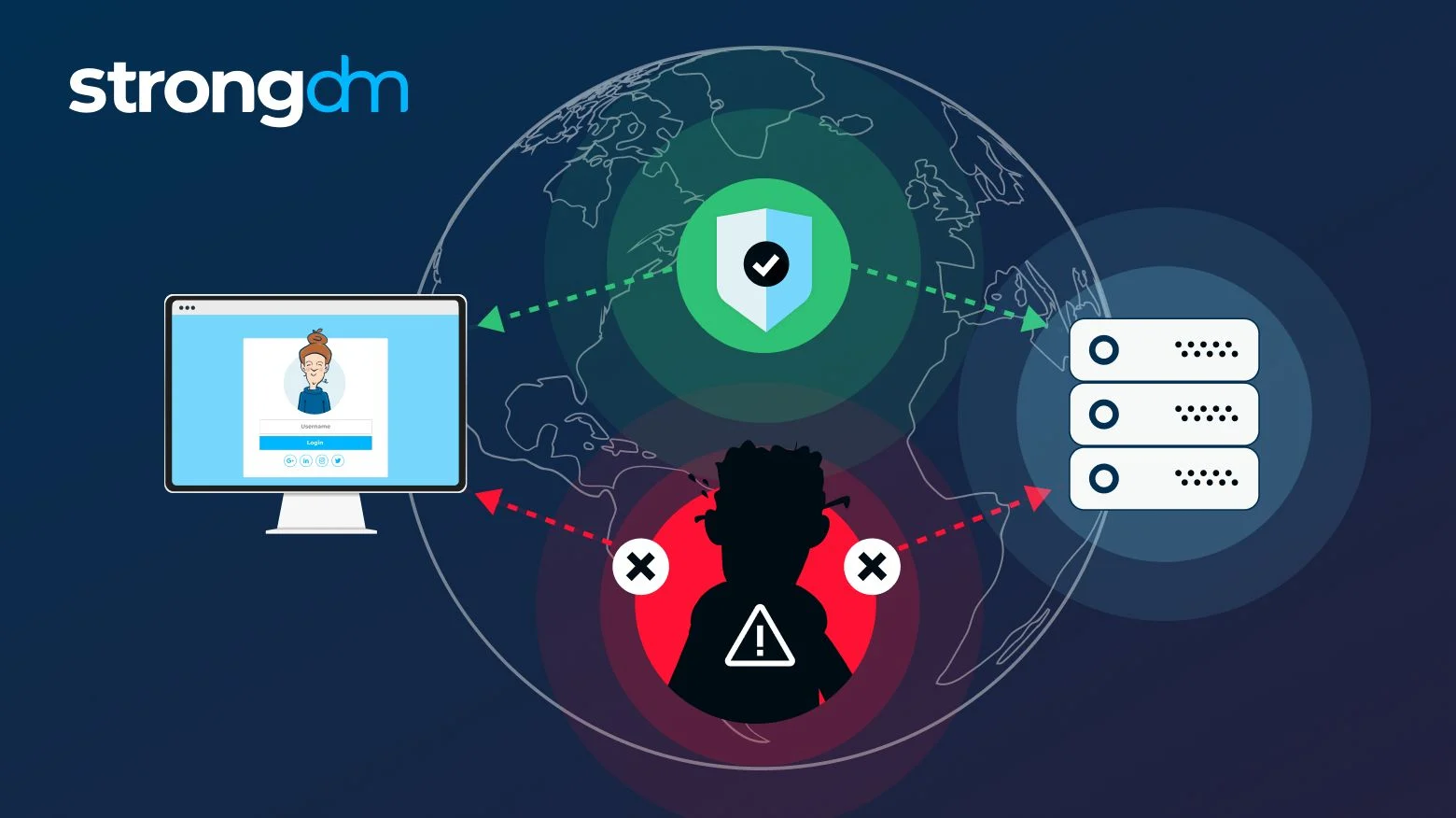
ManintheMiddle (MITM) Attack Definition, Examples & More StrongDM
Man-In-The-Middle (MITM) attack is one of many approaches that attackers or hackers use to steal or get unauthorized access to information. The MITM attack is a well-known attack where an attacker intercepts the information transmitted in a communication. At that point, the attacker can just resend the same information or modify it and re-send.. Quick Links. A man-in-the-middle (MITM) attack occurs when someone sits between two computers (such as a laptop and remote server) and intercepts traffic. This person can eavesdrop on, or even intercept, communications between the two machines and steal information. Man-in-the-middle attacks are a serious security concern.